USER DOMAIN ID
OBJECTIVE:
The objective of this policy is to lay down the procedure for issuing domain, internet account ID and password to authorized persons without affecting confidentiality and integrity of organization information residing on Computerized Systems over network.
SCOPE:
Accounts issued to all employees and contract employees are covered under the scope of this SOP.
RESPONSIBILITY:
Information Technology:
Responsible for implementing the laid procedure in this SOP and followed the laid procedure of SOP.
Function Users:
Adhere to the policy and procedure laid down in this SOP.
Function Head:
Approval of account ID for the Computerized System.
Head I.T. or Designee:
To review this SOP-IT.
Head QA or Designee:
To approve this SOP-IT.
ACCOUNTABILITY:
Head QA is accountable for the implementation and compliance of this SOP.
PROCEDURE:
Preamble:
Authorized person will be provided with account ID and password to access and communicate organizational information on Computerized Systems to improve productivity. The data on Computerized Systems are organizational information and are not private. Accounts are provided to use strictly for professional business purpose only to maintain the security over network. Solicitation of non-company business or any use of the account access for personal gain is strictly prohibited.
Policy:
Naming Convention:
The following naming convention for domain ID shall be as:
<firstname><lastname>@domain.com
(Domain = alps.com / alpslab.com).
When an ID with <firstname><lastname>@domain.com already exists then a new ID shall be created with following types:
| <firstname> + <initials of middle name><lastname> | <firstname><mi><lastname>@domain.com |
| <firstname><initials of middle name> + <lastname> | <firstname><mi><lastname>@domain.com |
| <firstname> + <initials of middle name><initials of last name> | <firstname><mi><li>@domain.com |
| <firstname><initials of middle name> + <initials of last name> | <firstname><mi><li>@domain.com |
Naming convention for long user names:
User names having more than 20 characters shall follow <firstname><initials of last name>@domain.com.
Active Directory Domain Policies:
When User logs on to the workstation following policies applied:
Password policy shall be set us:
| Policy Name | Description | Purpose |
| Default Domain Policy. | Enforced password history – 1 passwords remembered. | Previous 1 password (old password) cannot be used in new password. |
| Maximum password age – 30 days. | Password will expire in 30 days. | |
| Minimum password age – 0 days. | User can change the password anytime. | |
| Minimum password length between 8 to 14 characters. | Password should be minimum 8 characters and should not exceed more than 14 characters long. | |
| Password complexity requirements. | Not contain the user’s account name or parts of the user’s full name that exceed two consecutive characters.
Be at least six characters in length. Contain characters from three of the following categories: English uppercase characters (A through Z) English lowercase characters (a through z) Base 10 digits (0 through 9) Special characters (for example!,$,#,%) |
|
| Prompt User to change password before expiration – 5 days | User will be prompted to change the password 5 days before expiry |
- Account lockout policy shall be set as:
| Policy Name | Description | Purpose |
| Default Domain Policy. | Failed Logon Attempt – 5 consecutive attempts. | It determines 5 number of consecutive failed logon attempts that cause a user account to be locked out. A locked-out account cannot be used until the lockout duration for the account has expired. |
| Account lockout duration 10 minutes. | It determines the number of minutes a locked-out account remains locked out before automatically becoming unlocked. | |
| Reset Account lockout counter after 10 minutes. | It determines 10 minutes that must elapse after a failed logon attempt before the failed logon attempt counter is reset to 0 bad logon attempts. |
- Idle Session Timeout Policy shall be set as:
| Policy Name | Description | Purpose |
| Idle Session Timeout. | Enable Screen Saver. | If the workstation is idle for 5 minutes it will be locked. In case of window session is locked then the same user must unlock the workstation. Other users or I.T. Administrator cannot unlock the workstation. |
| Screen Saver Timeout 5 Minutes (Idle Time Out). | ||
| Password protects the Screen Saver. |
- Date & Time and Time Zone Policy shall be set as:
| Policy Name | Description | Purpose |
| Default Domain Policy / Restrict Time Zone. | Restrict users from changing date and time and time zone settings. Only Administrators are allowed to change the settings. | In any event user should not be able to change the time and time zone of the workstation or server. |
- Switch User Restriction Policy shall be defined as:
| Policy Name | Description | Purpose |
| Switch User Disabled. | Hide the Switch user button in the Logon User Interface, the Start menu and the Task Manager. Logged in user must logoff, if other user wants to login. | In an event logged in User must logoff, if other user wants to login. In case of window session is locked the same user must unlock the workstation. Other users or I.T. Administrator cannot unlock the workstation. |
- Time Server Policy shall be set as:
| Policy Name | Description | Purpose |
| Time Server. | Alps.com / alpslab.com domain to sync time from NTP server. | Alps.com / alpslab.com domain is installed on ESX host server). ESX host is set to sync time from NTP server.Alps.com / alpslab.com domain receives time from ESX host, which is in sync with NTP server. |
- Time Sync Policy shall be set as:
| Policy Name | Description | Purpose |
| Time Sync. | All systems in alps.com / alpslab.com to sync time from Primary Domain Controller. | All systems in alps.com / alpslab.com domain, time synchronization is done through alpslab.com domain controllers. |
- Activate the Audit account logon events shall be set as:
| Policy Name | Description | Purpose |
| Activate the Audit Account logon events. | To capture user logon logoff events. | Windows user logon logoff events shall be logged. |
Additional policies for LAB users (alpslab.com)
Impersonate a client after authentication policy shall be set as:
| Policy Name | Description | Purpose |
| Impersonate a client after authentication. | Assigning this privilege to a user allows programs running on behalf of that user to impersonate a client. Requiring this user right for this kind of impersonation prevents an unauthorized user from convincing a client to connect (for example, by remote procedure call (RPC) or named pipes) to a service that they have created and then impersonating that client, which can elevate the unauthorized user’s permissions to administrative or systems levels. | It is required for Instrument software. |
- Hide all local drives policy shall be set as:
| Policy Name | Description | Purpose |
| Hide all Local Drives. | Removes the icons representing selected hard drives from My Computer and Windows Explorer. Also, the drive letters representing the selected drives do not appear in the standard Open dialog box. | Hide Local drives on client workstations for lab users. |
- Restrict Removable Storage shall be as:
| Policy Name | Description | Purpose |
| Restrict the external storage devices i.e. CD / DVD and USB storage access. | To prevent users from accessing removable storage devices. | In any event User shall not be able to access CD / DVD and USB storage access. |
- Restrict the external storage devices i.e. CD / DVD and USB storage access:
| Policy Name | Description | Purpose |
| Restrict the external storage devices i.e. CD / DVD and USB storage access. | To prevent users from accessing removable storage devices. | In any event User shall not be able to access CD / DVD and USB storage access. |
- All windows user should have limited access rights:
| Policy Name | Description | Purpose |
| All windows user should have limited access rights. | The users with limited rights shall be prohibited from changing most computer settings, Cannot install software or hardware, but can access programs that have already been installed on the computer. | To a personal computer user who usually does work in a normal user account, and opens a privileged, password protected account (that is, a super user) only when the situation absolutely demands it. |
- Lockout Windows account in case of idle 5 minutes:
| Policy Name | Description | Purpose |
| Lockout Windows account in case of idle 5 minutes. | Enable Screen server, Screen saver timeout 5 minutes and password protect the screen server. | If the workstation is idle for 5 minutes it will be locked. In case of window session is locked then password must be entered to unlock the workstation. |
- Restrict the Control Panel:
| Policy Name | Description | Purpose |
| Restrict the Control Panel. | Users cannot start Control Panel or run any Control Panel items. It also removes Control Panel from the Start menu, and it removes the Control Panel folder from Windows Explorer. | In any event User shall not be able to access control panel. |
- Remove default games folder:
| Policy Name | Description | Purpose |
| Remove default games folder. | Remove unwanted application from workstation. | User shall not be able to access default games folder. |
- Remove Movie Maker and Windows Media Player:
| Policy Name | Description | Purpose |
| Remove Movie maker and Windows Media Player. | Remove unwanted application from workstation. | User shall not be able to access movie maker and windows media player. |
- Hide Recycle Bin:
| Policy Name | Description | Purpose |
| Hide Recycle Bin. | Removes the Recycle Bin icon from the desktop, from Windows Explorer, from programs that use the Windows Explorer windows, and from the standard Open dialog box. | Hide Recycle Bin on client workstations for lab users. |
- Remove Task Manager for Users:
| Policy Name | Description | Purpose |
| Remove Task Manager for Users. | To prevent accidental change in system. | User shall not be able to access task manager. |
- Audit logon events:
| Policy Name | Description | Purpose |
| Audit logon events. | To capture user logon logoff events. | Windows user logon logoff events shall be logged. |
Procedure of Account ID Creation:
The System Administrator will have access to create, modify and deactivate user ID.
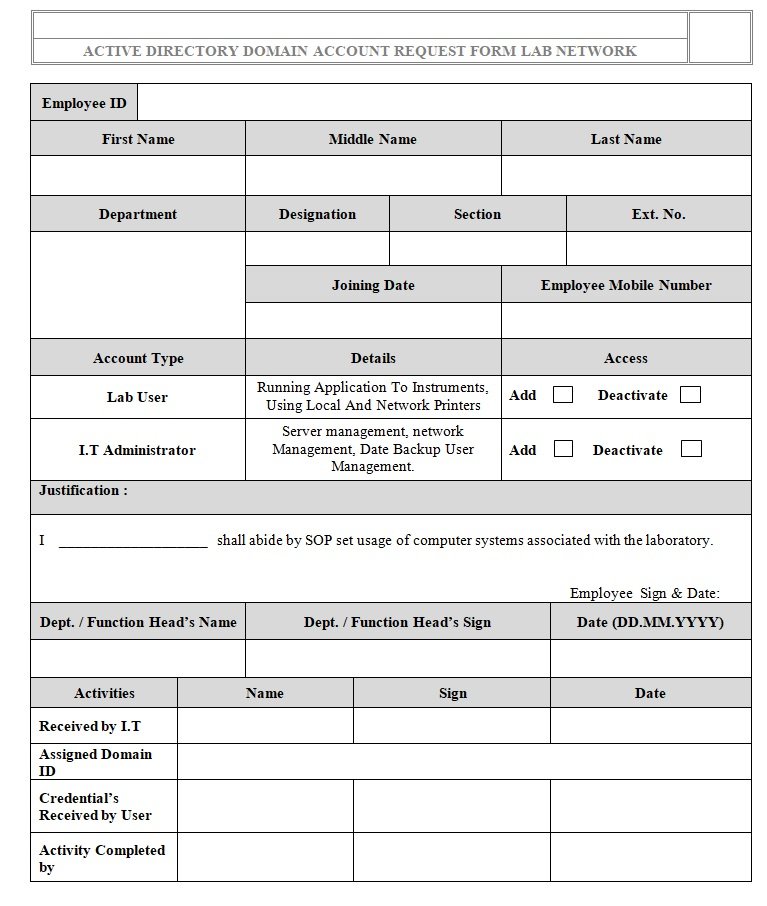
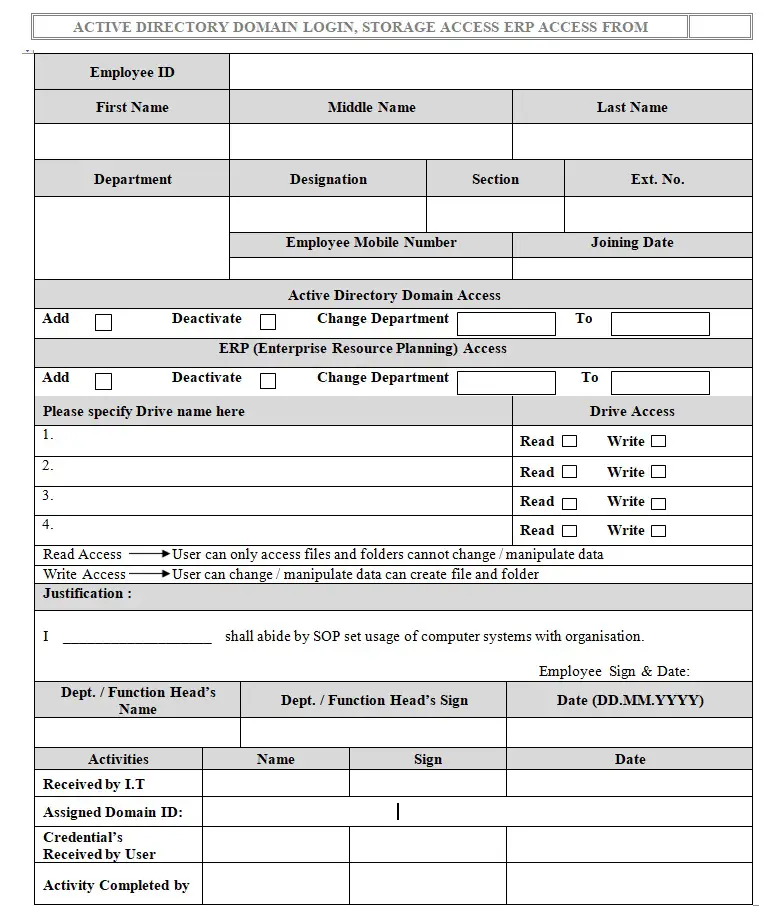
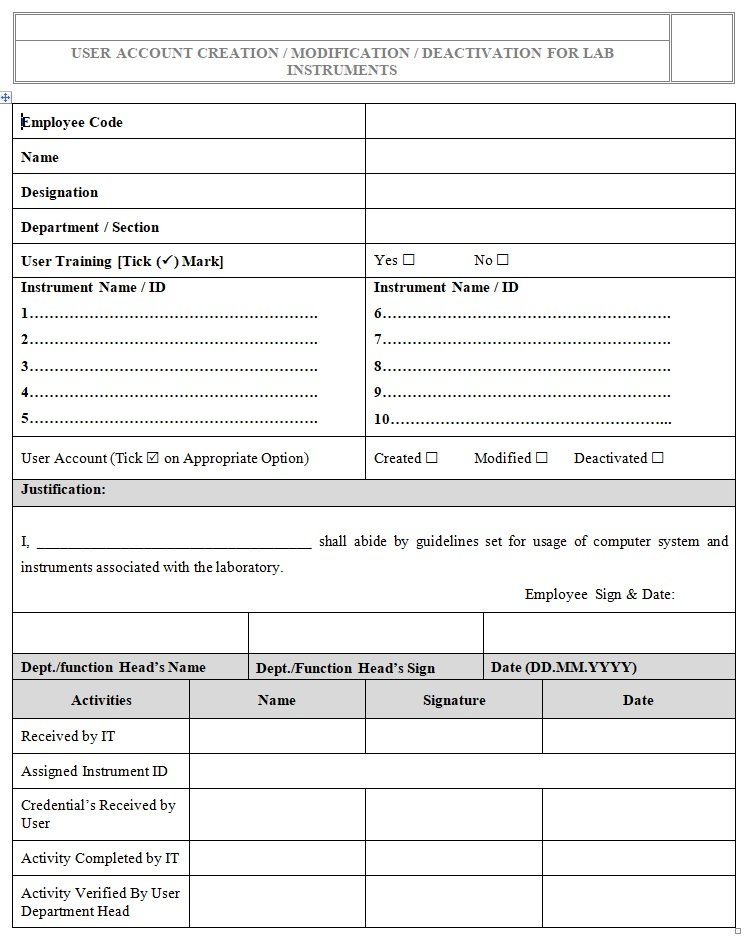
Users have to fill the Account Request Form (refer Annexure – I, Annexure – II, Annexure – III) as per requirement approved by respective department or function head and forward the same to respective site I.T. administrator.
Incomplete or invalid forms shall not be accepted by System Administrator.
Site I.T. will verify all the information and forward to I.T. Administrator.
On receipt of approved Account request Form System Administrator will generate and provide the account user ID and password to respective I.T. administrator.
T. administrator will further communicate to user for his / her account user ID and password.
If any change is required in existing user account, user shall fill the account request form.
Lab domain:
Additionally user shall sign, after receiving credentials, on Account Request Form.
After user sign, designated I.T. person forwards the account creation form to I.T. Administrator to complete the activity.
Process of Account ID Deactivation:
In case of E-mail and Active Directory Domain Login for deactivation of user id authorized designated function shall forward request to site I.T. administrator to delete the account (refer Annexure – I, Annexure – II, Annexure – III).
In case of GxP for deactivation of user ID authorized designated function or Q.C. person fills the form.
Forward for approval of Department Head.
Forward to I.T.
Designated I.T. person shall verify the information and forwards to the designated I.T. Administrator.
Designated I.T. Administrator deactivates the user ID.
User ID activation/deactivation will be verified by user department Head.
ENCLOSURE
| Annexure No. | Title |
| Annexure-1 | Active Directory Domain Account Request Form Lab Network |
| Annexure-2 | Active Directory Domain login and Storage Access Form |
| Annexure-3 | User Account Creation / Modification / Deactivation for Lab Instrument |
- ABBREVIATIONS:
| Abbreviation | Full Form |
| SOP | Standard Operating Procedure |
| QA | Quality Assurance |
| Rev. | Revision |
| NA | Not Applicable |
| NCR | Non-conformance Report |
| cGMP | Current manufacturing Practices |
| USB | Universal Serial Bus |
| DVD | Digital Versatile Disc |
| GxP | Good X Practices |
| IT | Information Technology |
| ID | Identification |
- REFERENCES:
- In House